3
Security Week: Azure Roles
Role Based Access Control is an important building block of a robust and secure system.
Traditionally permissions would be granted directly to a user account like "admin". This causes issues with accountability and audit of actions, and when individuals leave an organisation.
The best way to safely and practically implement security access controls, is to assign permissions to roles, and then assign roles to groups. These abstraction layers remove the case for accounts to be shared, and also reduce the risk of privileges being granted to individuals inappropriately.
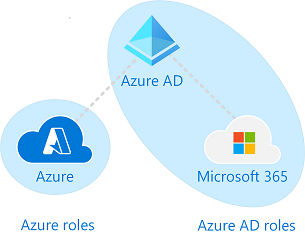
When talking about Roles in Azure, you'll hear about three different types: classic subscription administrator roles, Azure Roles, and Azure AD roles.
Classic Subscription administrator has widely been replaced by Azure Roles, which manages access to Azure resources.
For Azure Roles, there are over 60 built in which can be used for the majority of use cases. Where you need further granuality - Azure Roles supports creating custom roles.
Azure AD roles are similar - managing access to Azure Active Directory resources. They don't typically overlap with Azure Roles, and are fundamentally separate.
Azure AD Roles and Azure Roles are often managed by different groups within an organisation - so please plan ahead to ensure that the designs are complementary to oneanother.
Traditionally permissions would be granted directly to a user account like "admin". This causes issues with accountability and audit of actions, and when individuals leave an organisation.
The best way to safely and practically implement security access controls, is to assign permissions to roles, and then assign roles to groups. These abstraction layers remove the case for accounts to be shared, and also reduce the risk of privileges being granted to individuals inappropriately.
When talking about Roles in Azure, you'll hear about three different types: classic subscription administrator roles, Azure Roles, and Azure AD roles.
Classic Subscription administrator has widely been replaced by Azure Roles, which manages access to Azure resources.
For Azure Roles, there are over 60 built in which can be used for the majority of use cases. Where you need further granuality - Azure Roles supports creating custom roles.
Azure AD roles are similar - managing access to Azure Active Directory resources. They don't typically overlap with Azure Roles, and are fundamentally separate.
Azure AD Roles and Azure Roles are often managed by different groups within an organisation - so please plan ahead to ensure that the designs are complementary to oneanother.
