4
Security Week: Break Glass Accounts
We've talked about keeping malicious actors out of your platform for the last few days. But what about helping authorised users get back in - during an emergency?
Break glass accounts are superuser level user accounts created for use during an incident which prevents your standard administrator users from being able to log in.
Break glass accounts should be excluded from conditional access policies, should be created only in Cloud and not federated to on-premises, and should not have multi-factor authentication enabled. This ensures that even during an incident which would impact upstream connectivity - including those to first or third party MFA providers - you are still able to log in to your platform and recover.
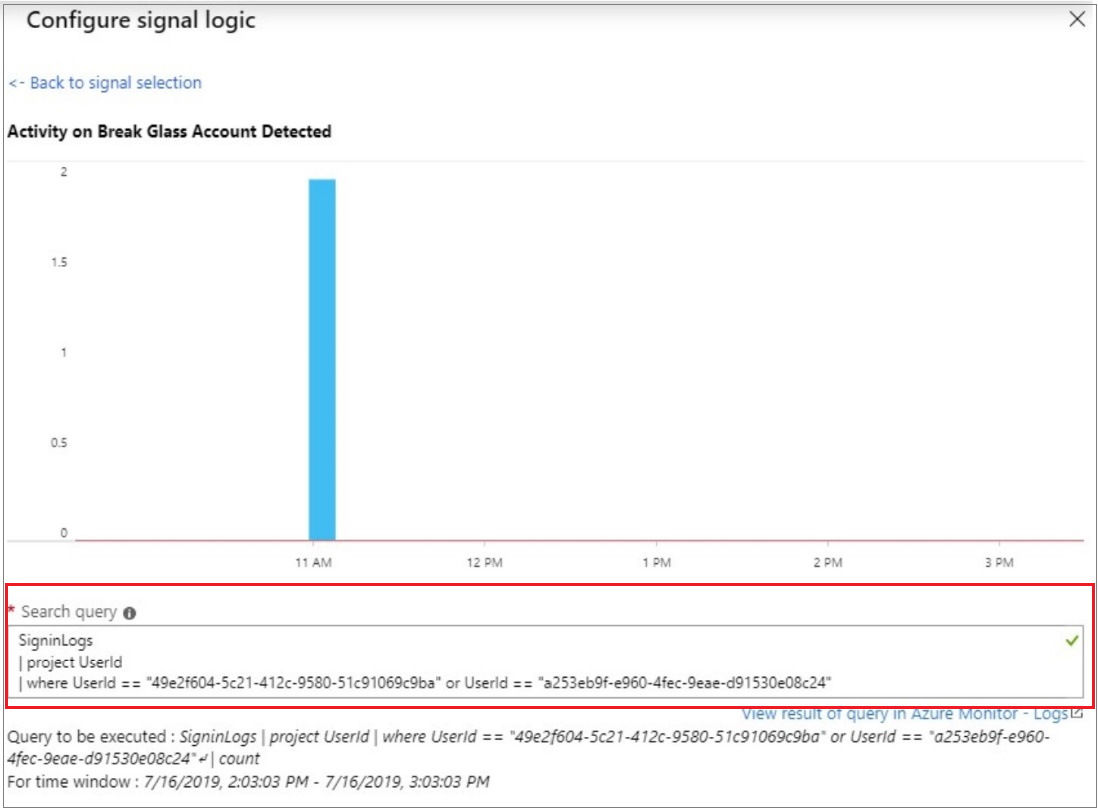
To ensure that the break glass account is only used for emergency purposes, you must have explicit alerting when the account is used. You can do this with Azure Log Analytics via email and other supported channels.
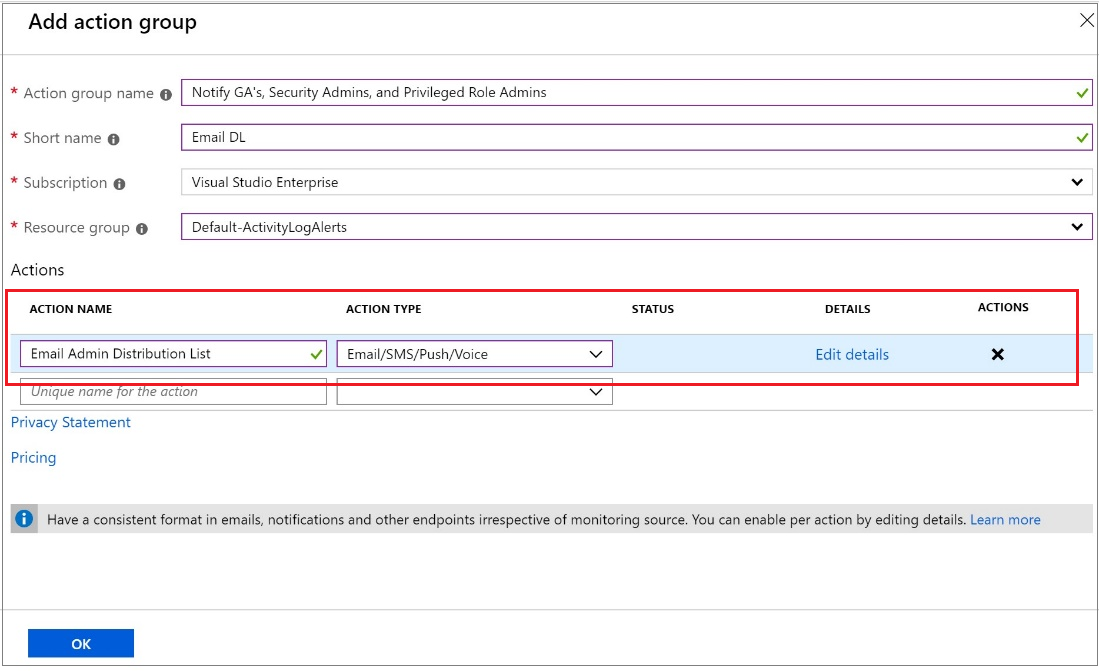
While I hope you never have to use - it is an important failsafe for production grade Cloud Ready systems.
Break glass accounts are superuser level user accounts created for use during an incident which prevents your standard administrator users from being able to log in.
Break glass accounts should be excluded from conditional access policies, should be created only in Cloud and not federated to on-premises, and should not have multi-factor authentication enabled. This ensures that even during an incident which would impact upstream connectivity - including those to first or third party MFA providers - you are still able to log in to your platform and recover.

To ensure that the break glass account is only used for emergency purposes, you must have explicit alerting when the account is used. You can do this with Azure Log Analytics via email and other supported channels.

While I hope you never have to use - it is an important failsafe for production grade Cloud Ready systems.
